Why Ransomware is Still Getting Through
Even in mature environments with EDR, SOC, and backups in place.
Ransomware continues to bypass well-funded defences. Here’s where traditional measures fall short and why stopping encryption is the crucial last line.
The Modern Ransomware Reality
Ransomware operators have evolved and no longer rely solely on smash-and-grab encryption.
Instead, attacks now typically involve:
✔ Initial access through phishing or vulnerabilities
✔ Privilege escalation within compromised environments
✔ Backup targeting to hinder recovery
✔ Coordinated encryption across critical endpoints, fast
By the time encryption begins, attackers have often:
✔ Disabled security controls
✔ Established persistence
✔ Identified high-value systems
✔ Bypassed perimeter monitoring
This means the final encryption stage happens rapidly, often in minutes. Detection alerts during this phase are frequently too late.
Why Traditional Defences Struggle
Most organisations focus on perimeter security and detection alerting. But once encryption begins, the clock is already ticking.
They rely on:
✔ Telemetry
✔ Log aggregation
✔ Cloud connectivity
✔ SOC triage
✔ Response playbooks
This model works well for visibility and investigation.
However, it assumes:
✔ Alerts are generated in time
✔ Controls remain operational
✔ Analysts respond immediately
✔ Network connectivity is intact
Ransomware groups actively target these assumptions. If attackers disable EDR, block outbound communications, or overload detection pipelines, response time increases even in mature environments. Encryption, once initiated, is extremely difficult to reverse.
The issue isn’t tooling. It’s time.
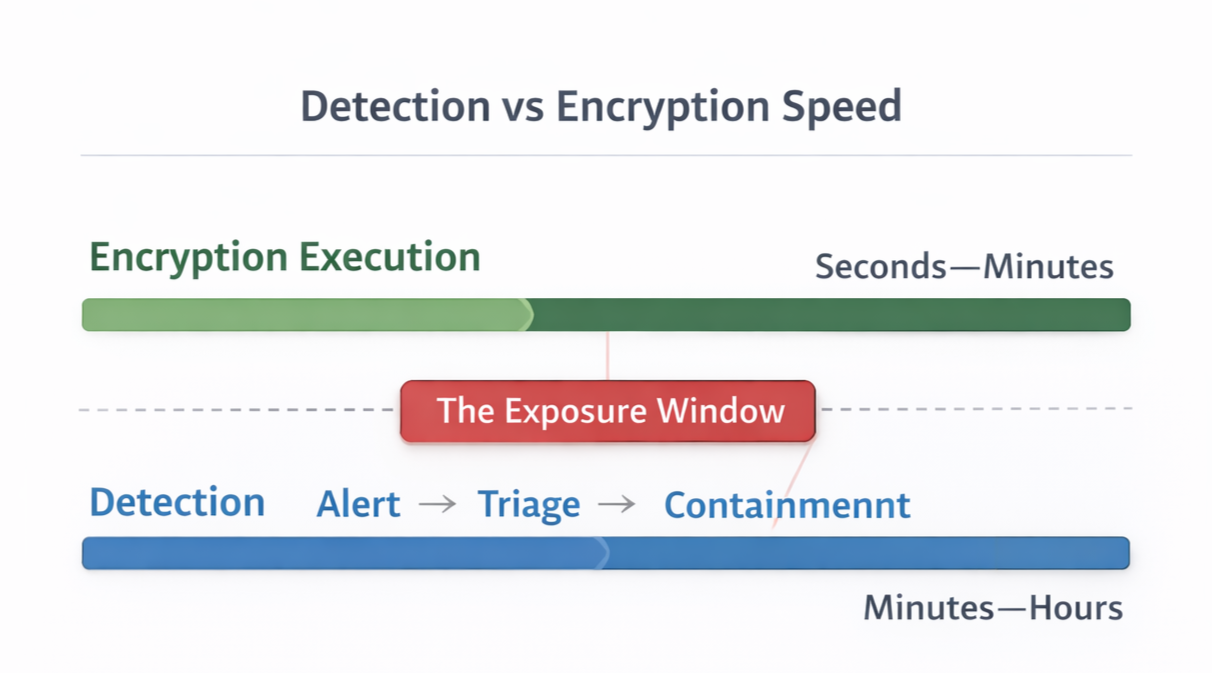
The Residual Risk Gap
This is where latent risks in ransomware defence become apparent.
Even in well-architected environments, there is a window between:
Malicious execution starting
SOC detection
Analyst investigation
Containment action
In that window, encryption can complete.
That exposure window is the Residual Risk Gap.
It is not a failure of the SOC ➡ It is not a failure of EDR ➡ It is an architectural limitation.
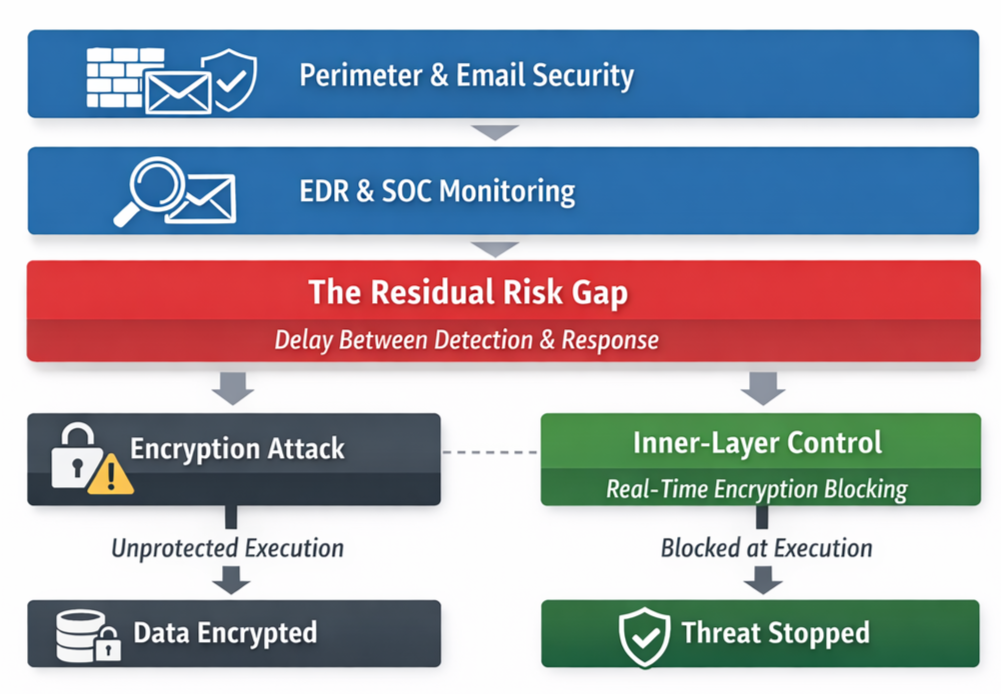
The Inner-Layer Control Model
To materially reduce ransomware risk, organisations require an additional control layer that:
✔ Operates independently of network connectivity
✔ Does not rely on cloud detection pipelines
✔ Cannot be easily disabled by attackers
✔ Acts at execution level on the endpoint
✔ Prevents unauthorised encryption activity in real time
Most security stacks focus on:
Detection
Alerting
Response orchestration
Few focus on guaranteed, real-time prevention of malicious encryption at execution level, independent of detection workflows.
That is the missing inner control layer.
The Peritus Approach
Peritus focuses specifically on closing the Residual Risk Gap.
Our approach centres on:
✔ Endpoint-level execution control
✔ Real-time encryption prevention
✔ Resilience even when connectivity is disrupted
✔ Integration alongside existing EDR and SOC tooling
Rather than adding more alerts or more detection noise, the objective is simple: If malicious encryption starts, it is stopped immediately.
This shifts ransomware defence from: “We will detect and respond quickly” to “Encryption cannot succeed.”
For organisations with strong security maturity, this represents the final layer of ransomware resilience
If Encryption Started Today - Would it be Stopped?
Ransomware doesn’t need multiple gaps. It only needs one window.